
An old adage says: “Don’t invest in what you don’t understand”. Many people interested in buying bitcoin and other cryptocurrencies have been put off by the apparent complexity of these new forms of money and the jargon involved in describing them. But cryptocurrencies don’t have to be inaccessible.
In a three-part series, we explain where cryptocurrencies came from, what powers their networks and how they are governed.
In this, the first article of the series, we examine the origins of cryptocurrencies.
Bitcoin and other cryptocurrencies draw upon a range of technologies invented in the previous decades. The internet is one (obviously), but what are the others?
Public key cryptography
A classic scene in a Cold War spy film shows the agent using a “one-time pad” to encrypt a message. On the one-time pad, the spy has a “key”: a set of instructions to convert his message into garbled (encoded) text.
The spy’s controller, the recipient of the message, has the same key and will use it to decrypt the message after receiving it. As its name suggests, the one-time pad is meant to be destroyed by the agent after use.
One-time pads are an example of symmetric key cryptography. By symmetric, we mean that the two people communicating both have to know the key in advance—otherwise the recipient of the message wouldn’t be able to unscramble it.
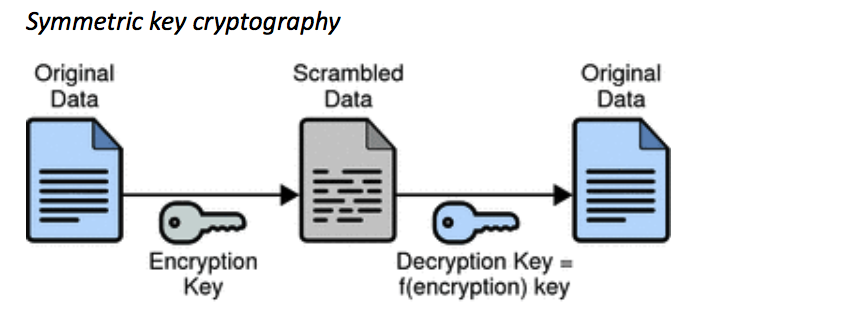
Symmetric key cryptography
Then an alternative way of encrypting messages was discovered. Public (also known as “asymmetric”) key cryptography, a theory set out in 1976 by Diffie, Hellman and Merkle, gave us a radically new approach to achieving secrecy in communication.
The advantage of asymmetric key cryptography, as opposed to the historic, symmetric method, is that it can operate at scale.
For two people to communicate using a public key cryptosystem, each needs a pair of keys: a public and a private key. As their names suggest, the public key is disclosed, while the private key is kept hidden.
The two keys, which are mathematically related, need to be used together. For example, if I want to send you a secret message, I encrypt my text with your public key and send the scrambled text to you. No-one can decipher it except you—by means of your private key.
Alternatively, I can encrypt a message with my private key, allowing anyone else to decrypt it with my disclosed public key. Why would I want to do that? By sending the original message, plus the one I encrypted with my private key, what I’ve done is to add an effectively unforgeable digital signature to my message.
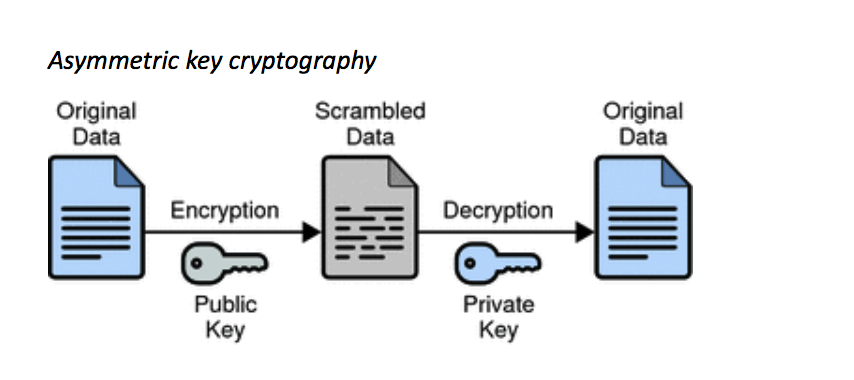
Asymmetric key cryptography
The advantage of asymmetric key cryptography, as opposed to the historic, symmetric method, is that it can operate at scale. You can use it for secure electronic communication between people who don’t know each other, and for a large network of participants. Cryptocurrencies are one application of this idea.
By contrast, symmetric key cryptography wouldn’t be an adequate technology for internet-based commerce: it wouldn’t be feasible to share the key between each pair of participants in advance, nor to change the key each time a transaction took place.
One-way functions
It was one thing setting out public key cryptography in theory. But to put public key schemes into practice, cryptographers needed to find the right kind of mathematical ‘scrambling’ schemes to produce the public and private keys necessary to encode and decipher data.
After a few experiments, they eventually settled on a mathematical operation called a “hash” function. Hash functions are easy to perform in one direction, but effectively impossible to reverse.
The output of a hash function (called, unsurprisingly, a “hash”) looks random, but it’s not. You can easily verify that the input of a hash function translates into a given output. But getting from the output to the input is effectively impossible—it’s like trying to unmix the beaten eggs in an omelette bowl.
Where do we get hash functions? Many of the most popular ones have been developed and disseminated by governmental agencies, a fact that has given rise to some conspiracy theories (for example, that the US National Security Agency is the creator of bitcoin).
The hash function used by bitcoin is called “Secure Hash Algorithm 256” or “SHA-256”. It was released by the US National Institute of Standards and Technology in 2002.
With a hash function you can’t get from B to A, but if you start at A you will get to B.
SHA-256 maps input data to an output of exactly 64 characters in length. Let’s apply SHA-256 to the word “cat” (you can do this yourself, if you want to check). The hash is:
175cc6f362b2f75acd08a373e000144fdb8d14a833d4b70fd743f16a7039103f
Then let’s make the smallest change to the input, making the first “c” in “cat” a capital letter. With “Cat” as the input, SHA-256 produces the following output:
58f0c2c4c5782f3c6b9e4f185e03d7e08690f337d74a0732ea71b8d37c39fcfe
The hash of “Cat” looks totally different from the hash of “cat”. By making the smallest change to the input, we’ve made the output change completely, and in an apparently random way. But, remember, with a hash function, while you can’t get from B to A, if you start at A you will get to B. And anyone, anywhere can verify this is the case.
The blockchain
Cryptocurrencies make use of, and depend upon the ability of hash functions to “fingerprint” data in a non-reversible way.
Cryptocurrencies perform a neat trick: by using hash functions to link together datasets of transactions in the relevant cryptocurrency (these datasets are called “blocks”), they build up a history of the currency that is both irrevocable and transparent. This history is called a blockchain.
The latest block in the chain only includes details of the latest transactions in the currency. But it also includes an unforgeable link, via a hash, to the previous block, where we can then go to check the previous period’s transactions. And we can repeat this process over and over until we reach the first (or “genesis”) block of that particular currency. The full transaction history of bitcoin is therefore available for anyone to see, by means of downloading the relevant software.
A distributed consensus mechanism
To build a cryptocurrency we also need a consensus mechanism.
Why? Bitcoin is a distributed currency: its transactions are recorded on all the nodes in the network—around 12,000 at the latest count. But what stops the nodes from disagreeing with each other on which transactions have taken place?
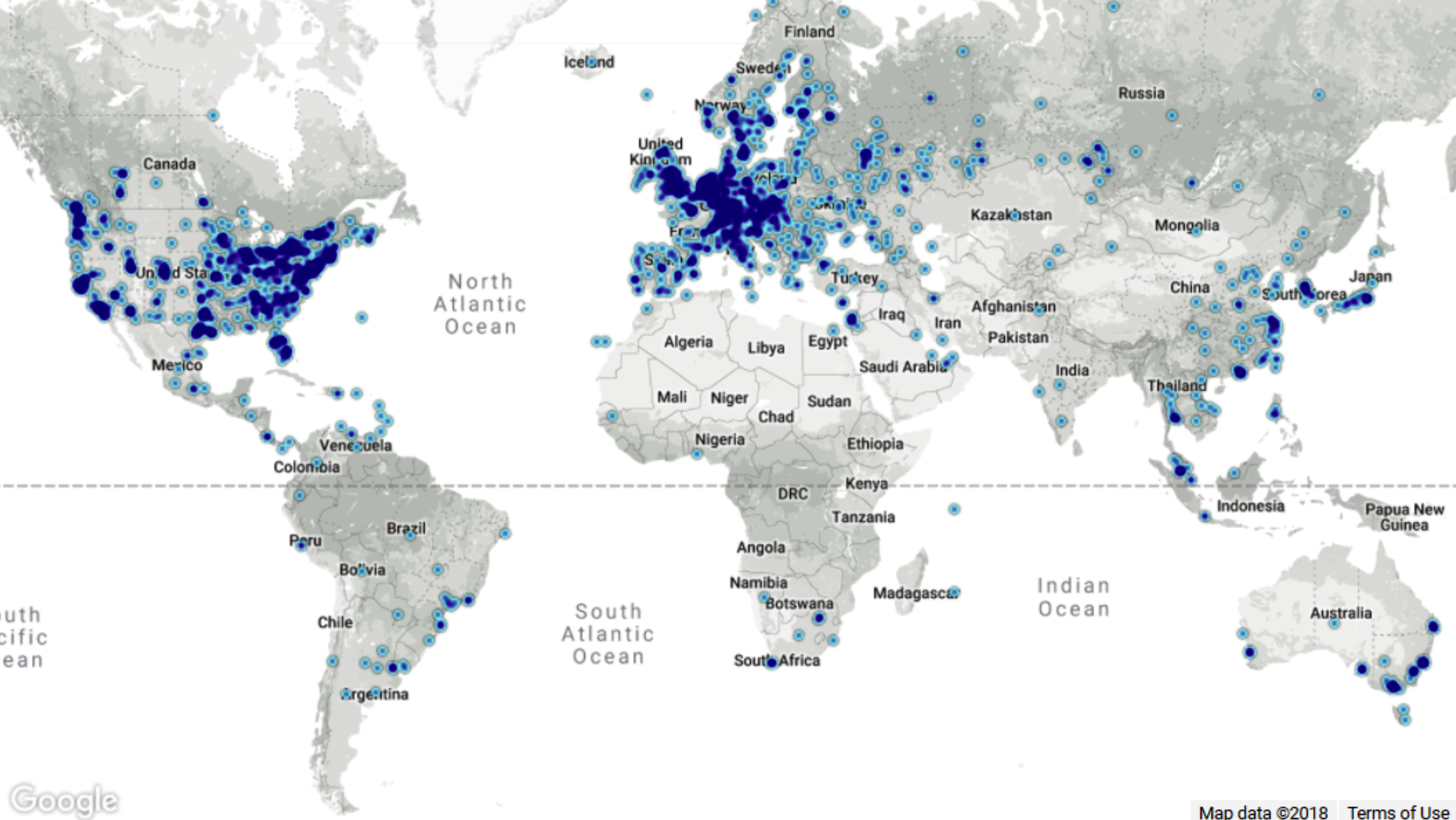
A global map of bitcoin nodes
This is potentially fatal flaw in a currency based on a distributed network. If the nodes in the network didn’t agree on the transaction history, fraudsters could spend the same money twice or more—sending one set of payment instructions to some nodes and a second set to others, and so on. Under such circumstances, the currency associated with the network would be worthless: no one would trust it.
Many observers see the ‘censorship-resistant’ quality of the bitcoin network as its most important technological innovation.
An obvious answer to this challenge would be to give one node, or some other kind of central authority, the power to decide what constitutes the correct history. In fact, this is how the existing financial system operates. Central banks, banks, securities settlement systems and payment institutions like PayPal or Visa all log (and, effectively, approve) financial transactions on the basis of a single central set of records.
But this what the designer(s) of bitcoin, the person or people called Satoshi Nakamoto, specifically wanted to avoid. Why? Because using a distributed network, rather than a central authority, makes bitcoin very difficult to censor, shut down or control.
Nakamoto wanted to put currencies out of the control of governments and central banks, and in the hands of a computer-based network operating under preassigned and transparent rules. Many observers see the “censorship-resistant” quality of the bitcoin network as its most important technological innovation.
But to make the computers constituting the cryptocurrency network work in collaboration, rather than attempting to defraud one another, an incentive scheme is needed. In bitcoin’s case, nodes in the network compete to earn a monetary reward in the form of coins and transaction fees. Getting the reward is conditional on proving (as a node) that you’ve spent a certain amount of energy. We explain bitcoin’s “proof-of-work” mechanism in the second article of this three-part series.









